
Add to Cart
Deep Packet Inspection VPN by Network Visibility Software Tools of Network TAP
With network communication technology progress and development, network communication has entered the era of big data, how to monitor all kinds of business system of communication data transmission quality in the large data flow, and the category of vast amounts of network traffic data exists in the small amount of malicious traffic detection, avoid malicious communications for hosts, network devices, the root of security threats, and the communication content theft.Is the network management must face a difficult problem.
It is the law of nature that there is a spear to attack and a shield to defend itself.With the advent of big data, traditional real-time detection and defense are no longer capable of identifying subtle anomalies in massive data.Therefore, the real-time backup of original communication data gradually shows its necessity, and the backtracking analysis technology based on time window to detect the depth of packets is the microscope to find abnormal data.
Introduction to DPI technology
DPI(Deep Packet Inspection) technology is based on the traditional IP Packet Inspection technology (detection and analysis of Packet elements contained between OSI l2-l4), which adds application protocol recognition, Packet content detection and depth decoding of application layer data. Deep Packet Inspection (DPI) is also a sophisticated network packet filtering technique used to analyze the contents of data packets as they pass through a network. Unlike traditional packet filtering, which only examines the header information, DPI inspects the payloads of packets to gather detailed information about the data being transmitted.
By capturing the original packets of network communication, DPI technology can use three kinds of detection methods: "eigenvalue" detection based on application data, recognition detection based on application layer protocol, and data detection based on behavior pattern.According to different detection methods, unpack and analyze the abnormal data that may be contained in the communication packet one by one to dig out the subtle data changes in the macro data flow.
DPI supports the following applications:
• the ability to manage traffic, or control end-user applications such as point-to-point applications
• security, resources, and licensing control
• policy enforcement and service enhancements, such as personalization of content or content filtering
The benefits include increased visibility into network traffic, which allows network operators to understand usage patterns and link network performance information to providing usage base billing and even acceptable usage monitoring.
DPI can also reduce the overall cost of the network by reducing operating expenses (OpEx) and capital expenditures (CapEx) by providing a more complete picture of how the network is operating and the ability to direct or intelligently prioritize traffic.
• Cybersecurity: Used for threat detection, intrusion prevention
systems (IPS), and monitoring for data breaches.
• Traffic Management: ISPs and organizations use DPI to manage
bandwidth and enforce quality of service (QoS) policies.
• Compliance: Ensures adherence to legal and regulatory requirements
by monitoring sensitive data flows.
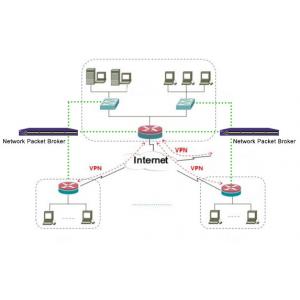
Deep Packet Inspection(DPI) in VPN Virtual Private Network Application
VPN is a remote access technology, which simply means using public network to set up private network.For example, if an employee of a company is on a business trip and wants to access server resources on the Intranet, such access is remote.
In the traditional enterprise network configuration, to carry out remote access, the traditional method is to rent DDN (digital data network) line or frame relay, such a communication scheme will inevitably lead to high network communication and maintenance costs.For mobile users (mobile office workers) and remote individual users, generally through the dial-up line (Internet) access to the enterprise's LAN, but this will inevitably bring security risks.
Let the non-local staff access to the Intranet resources, the use of VPN solution is to set up a VPN server in the Intranet.After connecting to the Internet locally, the non-local employees connect to the VPN server through the Internet, and then access the enterprise Intranet through the VPN server.In order to ensure data security, the communication data between VPN server and client is encrypted.With data encryption, can think the data is in a special secure transmission of data link, like specially set up a private network, but is actually a public link VPN are using the Internet, so called VPN virtual private network, its essence is to use encryption technology in public encapsulation out a data communications channel.With VPN technology, users can use VPN to access internal network resources as long as they have access to the Internet, no matter they are traveling or working at home. This is why VPN is so widely used in enterprises.
Recommend Network Packet Broker for Deep Packet Inspection VPN by Network Visibility Software Tools
Network Packet Broker Specifications
| NT-FTAP-48XE NetTAP® NPB Functional Parameters | ||
| Network Interface | 10GE SFP+ ports | 48 * SFP+ slots; support 10GE/GE; support for single and multi-mode fiber |
| Out of Band management interface | 1* 10/100/1000M electrical interface; | |
| Deployment mode | 10Gigabit spectral capture | Support 24*10GE bidirectional fiber links capture |
| 10Gigabit Mirror span capture | Support up to 48 mirror span traffic ingress | |
| Optical Splitter input | Input port can support single-fiber ingress; | |
| Port multiplexing | Support input ports simultaneously as output ports; | |
| Traffic output | Support 48 *10GE ports traffic output; | |
| Traffic replication / aggregation / distribution | support | |
| Link QTYs supporting Mirror replication / aggregation | 1 -> N link traffic replication (N <48) N-> 1 link traffic aggregation (N <48) G Group(M-> N Link) traffic replication and aggregation [G * (M + N) <48] | |
| Distribution based on traffic identification | support | |
| Distribution based on IP / protocol / port Five tuple traffic identification | support | |
| Distribution strategy based on protocol header the key labeled traffic identifies | support | |
| Ethernet encapsulation independence | support | |
| CONSOLE network management | support | |
| IP/WEB network management | support | |
| SNMP network management | support | |
| TELNET/SSH network management | support | |
| SYSLOG protocol | support | |
| User authentication function | Password authentication based on user name | |
| Electric(1+1 Redundant Power System-RPS) | Rated supply voltage | AC110-240V/DC-48V [Optional] |
| Rated power frequency | AC-50HZ | |
| Rated input current | AC-3A / DC-10A | |
| Rated power function | 200W | |
| Environment | Operating Temperature | 0-50℃ |
| Storage Temperature | -20-70℃ | |
| Operating Humidity | 10%-95%,Non-condensing | |
| User Configuration | Console Configuration | RS232 Interface,115200,8,N,1 |
| Password authentication | support | |
| Rack Height | Rack space (U) | 1U 485mm*44.5mm*350mm |
NT-FTAP-48XE Network TAP NPB.pdf
Plz contact NetTAP® directly to Optimize your Network now!
